



The Need for Security First Perspective
The software industry has a worldwide market with different domains, platforms, and features to smoothen business processes. Every software industry tries to provide advanced features and makes efforts to launch solutions in the market within a short period. However, due to such fast and volatile market conditions, application/product security remains the most snubbed area since the last decade.
Application security plays a vital role in business areas such as customer trust, customer satisfaction, sensitive customer data, and gaining market capture. Any compromise directly affects the business and product’s brand value. To avoid landing up in a bad situation, organizations are allocating separate budgets for product security.
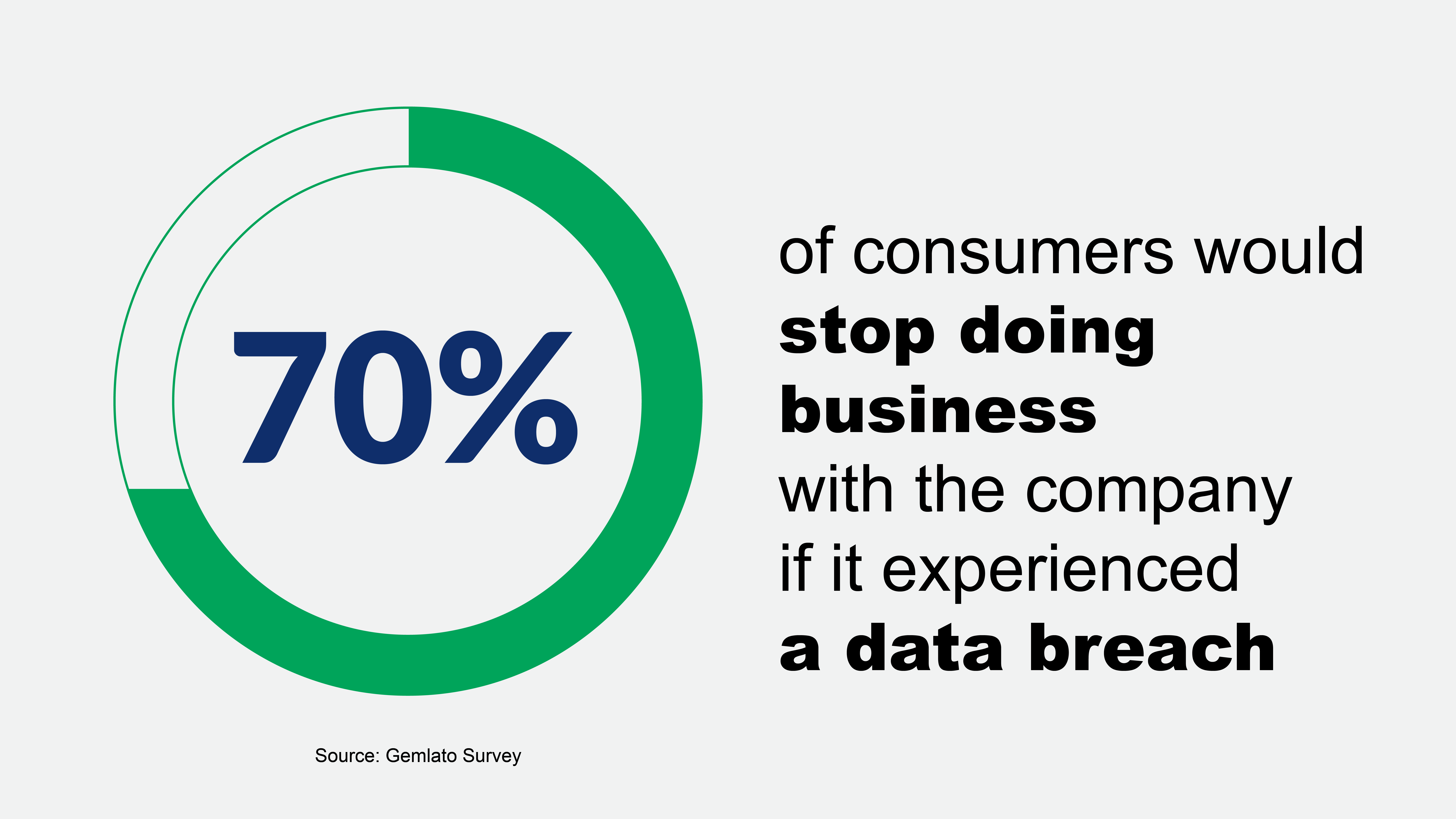
With this changing trend of the market, engineering teams including developers, architects are considering the importance of application security. Many developer groups provide patches/fixes post-finding breaches in their application. This lack of awareness towards security, costs organizations, demolishes the brand trust. Engineering teams can avoid this by taking precautions while designing & developing software before undergoing security analysis or before GTM.
This is the first part of the blog series. In this blog, we will explain the perspective shift in an engineering team’s SDLC journey during the design/development phase by focusing on best security practices to avoid any breach or vulnerability.
Awareness of Vulnerabilities & Assessment
Vulnerability is a weakness that can be exploited by a threat actor. This can be an attacker who crosses privilege boundaries within a computer system. The process of finding, assessing, categorizing these vulnerabilities is called Vulnerability Assessment.
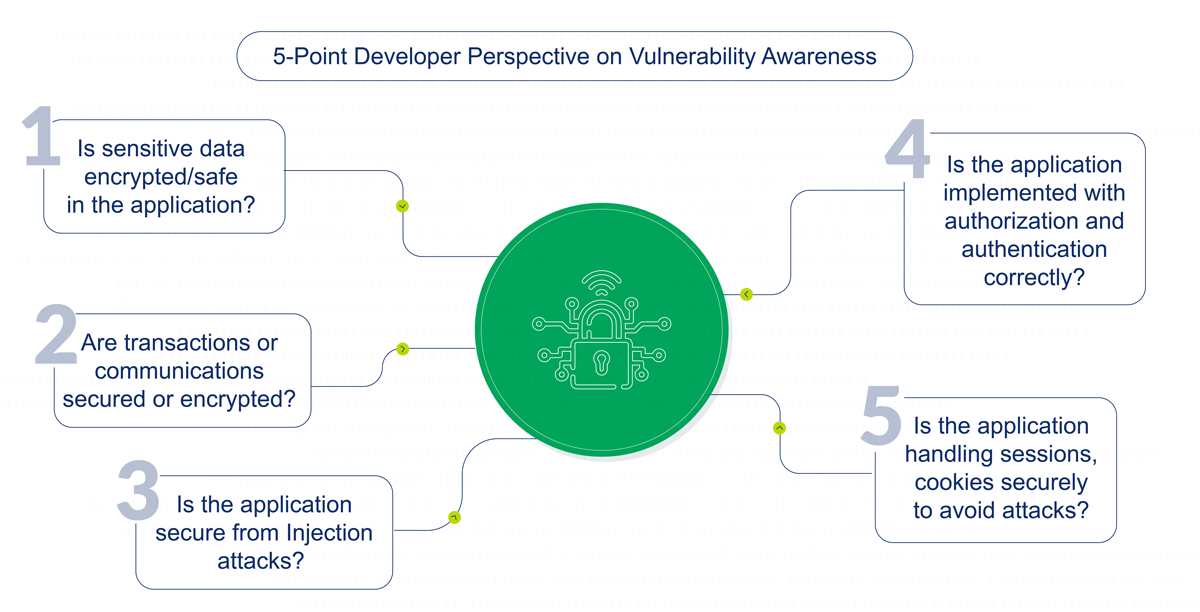
Every developer must be aware of the vulnerabilities and their impact during software development. This includes overall education by asking the following 5-point questionnaire:
1. Is sensitive data encrypted/safe in the application?
2. Are transactions/communications encrypted?
3. Is the application implemented with authorization and authentication correctly?
4. Is the application secure from any kind of Injection attacks?
5. Is the application handling sessions, cookies securely to avoid attacks?
Developers Negligence: An Added Cost to Organization
A superior quality product or software needs an allocated budget for its lifecycle from requirement analysis to go-to-market. This depends on many factors such as - business requirements, resources, development timeframe.
Apart from these main factors, many indirect factors affect the software development budget. Some of them can be mentioned as bugs introduced by developers, re-testing, and re-deployment time after the bug fixing phase.
Many organizations follow the best practice of allowing developed software to undergo security scans before launch. This step of the scan assesses the possibility of having breaches in the application.
This can enable the developer to rework the issues. However, we can reduce the timeline of re-working on security issues by educating developers. This can be enhanced with best-secured coding practices instead of only relying on scan reports. A developer’s secured perception will save a major time and cost to apply security patches and help the organization.
Securing Software Development Life Cycle
In a simple scenario, every software undergoes Software Development Life Cycle (SDLC) based on organization policies. However, if the organization talks about processes to improve cost-effectiveness during software development, then securing SDLC will help the organization to save costs by 25% to 30%. These SDLC phases can be re-structured from a security perspective as shown in the diagram below:
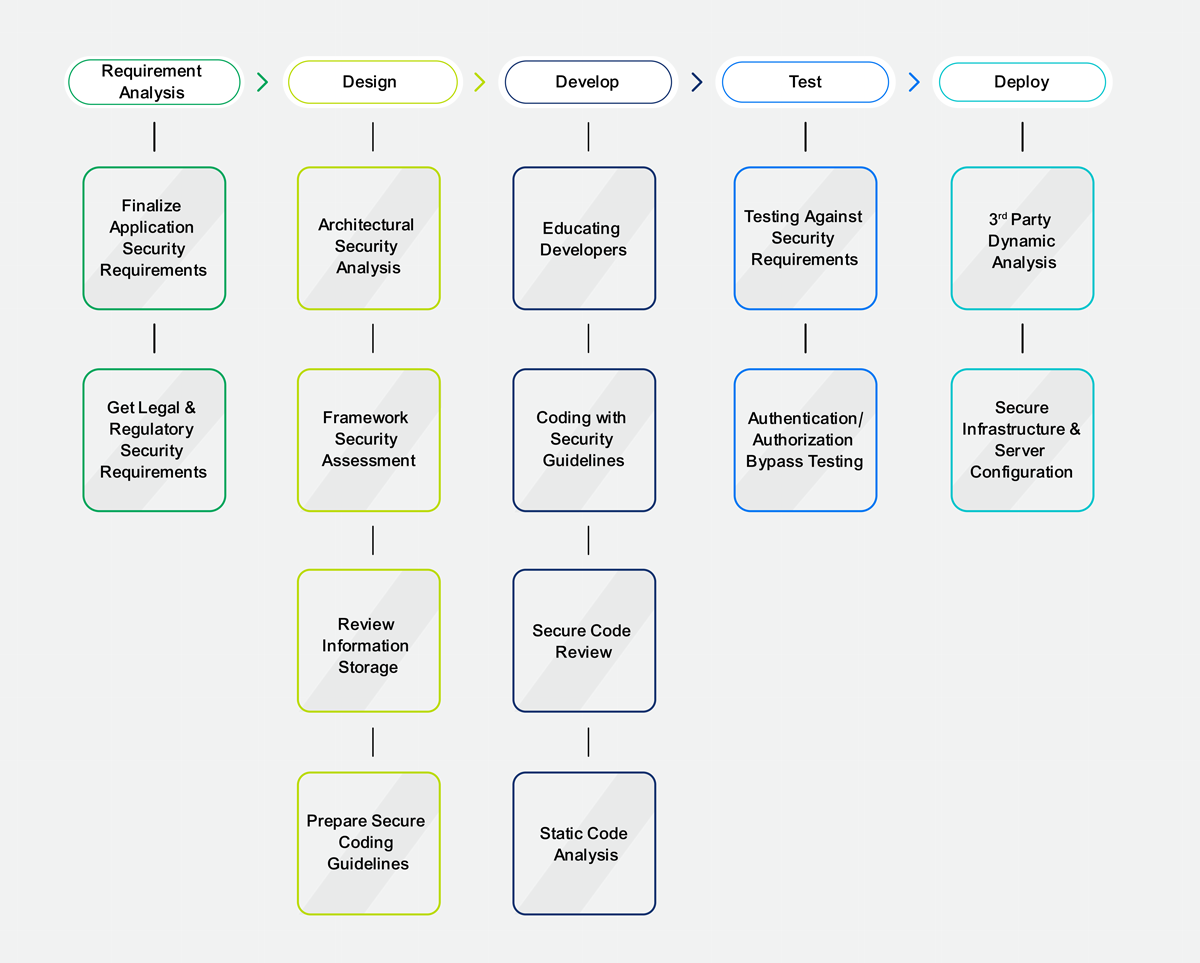
Requirement Analysis
In addition to assessing, analyzing, and finalizing the customer’s business requirements, the business analysts need to focus on finalizing Application Security Requirements. These include:
- Determining environments in which applications will be used.
- Finalizing application user’s scope, use cases along with authentication & access scenarios.
- Understanding and adopting respective government’s legal and regulatory protocols, policies.
- Considering sensitive information storage rules and regulations like GDPR policies.
Design
The application architect plays a very crucial role in the design phase. It has been said that the design is the base of any application. The architect must design the application by considering security requirements as well as business requirements. While designing the application, the architect must focus on different perspectives like:
- Analyzing the end-to-end design/architecture from a security perspective.
- Assessing frameworks, technologies for known vulnerabilities before finalizing.
- Reviewing and assessing sensitive information storage for any flaws.
- Preparing & finalizing secure coding policies and guidelines which need to be used while developing.
Develop
This is another crucial phase followed by the Design phase. This is also called as implementation phase as the application modules get implemented as per design in this phase. Every developer must be educated to follow secured coding practices.
Informed developers will have a secured perspective while developing and reviewing code for modules being implemented. The development phase should be secured with the following perspectives:
- Educating developers for security perspectives.
- Coding with Security Guidelines finalized by the organization or the architects.
- Secure code review to be followed.
- Conduct Static Code Analysis to find out any vulnerabilities in the early stage.
Test
This is the quality assurance phase post-development. Quality analysts assure application quality by testing each feature, module against the prepared test plan. While testing application, every analyst must focus on testing modules with a security perspective like below:
- Testing each feature against security requirements finalized during the requirement analysis phase.
- Performing rigorous testing to find out a security flaw, vulnerabilities, test for bypassing authentication and authorization, etc.
- Usage of Browser-specific Developer Tools for exploring security testing for a web application, different password policies, HTTP header contents, etc.
Deploy
Once the application is stable and tested for its quality, the application will be deployed on different environments. These include Staging, Production, etc. This phase also needs to focus on security precautions similar to other phases in SDLC as below:
- Conduct 3rd party Dynamic Scan analysis for an application like HP Fortify, Veracode DAST.
- Ensure that Infrastructure & Server Configurations are completely secured.
Security Success Story
When we talk about the process changes, it must be justified with examples of success stories. Recently, one of the well-known organizations released its product with new features successfully. Post-release, the organization, and the customer decided to go for a security scan together. Post-scan analysis, the organization had to put complete efforts to re-design, re-develop, and re-test for a security patch.
With these new security changes, the organization gained the trust of multiple customers, enhanced brand value during the business. So, the organization adopted it as a mandatory practice to have Security implementation in SDLC. This changed the developer’s perspective while developing along with the reduced cost of re-design, re-development, and re-testing.
Way Forward
We can make sure about changing architects’ and developers’ perspectives towards product security by introducing security perspectives in each SDLC phase. Informed and trained resources can achieve organizational growth quickly in terms of saving time and cost involved in re-work. Organizations can launch their solutions in the market in quick time, with more brand value, with a more secured solution, and with few chances of attacks by rival attackers.
Xoriant brings decades of security experience with the cutting-edge new tools and technologies to protect your assets from legacy systems to cloud-native and mobile apps. We ensure that your business is free from actual and potential vulnerabilities.
Want to know more about how Xoriant can help you with security best practices and standards?
Connect With Xoriant Security Experts





 View Previous Blog
View Previous Blog




