



Simplifying Compliance: How CISO Dashboards Streamline Regulatory Reporting
Globally, the cyberthreat landscape continues to evolve in terms of both the frequency and sophistication of attacks. Hackers are deploying various advanced techniques, including AI-powered attacks and zero-day exploits to exploit system vulnerabilities. In 2024, cybercrime is estimated to cost businesses around $9.5 trillion. This is projected to rise to $15.63 trillion by 2029.
With each passing year, CISOs have to deal with more complicated forms of cyberattacks. Security regulations are also making their job more "complex." For instance, the SEC's latest cybersecurity disclosure requirement mandates them to report any significant cyber incident within 4 business days. There’s no question that staying compliant is becoming a race against the clock – but does it have to be this way?
For CISOs, changing regulatory compliance requirements demands greater transparency across all operational areas to enable more timely response as well as faster and more complete reporting. However, multiple studies show that only a fraction of cybersecurity leaders are “confident” or “very prepared” to deal with the cybersecurity compliance standards in their organization. This inability to meet the necessary standards further complicates the organization’s security posture and assessment.
CISOs face challenges in enforcing compliance in an ever-changing complex IT environment. Using the zero trust approach to keep attack surfaces to a minimum, CISOs deploy several security controls and would like to track their effectiveness. Tracking the key performance and risk indicators in real time is a huge challenge, and reporting it is even bigger, making it difficult to know the regulatory compliance status in real time. That’s where a carefully considered dashboard approach can come in handy.
CISOs try to create such dashboards manually every time they need to report the cyber security compliance status to the board, which is a time-consuming and error-prone approach.
Designed to improve cybersecurity compliance management, a CISO dashboard provides real-time insights that enable CISOs to manage their cyber risks proactively. Here's how a CISO dashboard simplifies regulatory reporting and compliance.
Defining the CISO Analytics Dashboard
Simply put, a CISO analytics dashboard presents critical security metrics and KPIs (in a visualized format), which indicate the effectiveness of the organization’s current cybersecurity program. By analyzing real-time data, this dashboard provides a comprehensive picture of the company’s security posture, and highlights the critical areas for improvement and attaches the organizational context to it.
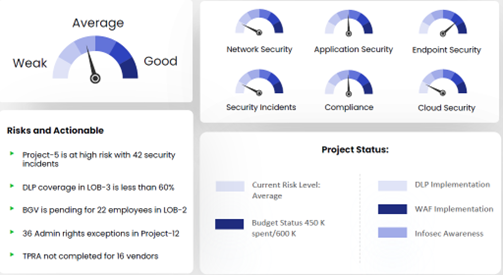
Here are some of the real-world benefits of a CISO analytics dashboard for CISOs:
1. Improves risk assessment and management.
With a CISO analytics dashboard, CISOs can evaluate and manage their cyber risks effectively. The dashboard provides real-time insights into the company's security posture – thus enabling cybersecurity teams to detect vulnerabilities and threats. Overall, CISO dashboards speed up the identification of security risks by 25-30%.
By evaluating insights from its risk assessment capability, CISOs can focus on security areas with the maximum risk factor and devise corrective measures.
2. Improves data governance and security.
With the CISO analytics dashboard, CISOs can also improve data governance with real-time visibility into data entering (or exiting) their IT ecosystem. Moreover, CISOs and managers can delve into the shared files and produce compliance reports related to the sharing of sensitive data.
Besides fulfilling compliance requirements, the CISO dashboard enables CISOs to measure the effectiveness of their data security initiatives.
3. Efficient monitoring and tracking of security metrics and KPIs in real time.
Effective security monitoring and decision-making are impacted by a lack of standardized metrics and compliance reporting. A CISO dashboard overcomes this limitation by enabling CISOs to track metrics relevant to their security objectives. Additionally, an automated security dashboard reduces the manual workload for security teams.
Through continuous monitoring of security metrics and KPIs, CISOs can measure the effectiveness of their security initiatives and identify areas of improvement. With internal gap analysis, CISOs can compare the cybersecurity practices of various business units, divisions, or geographically distributed teams in a complex enterprise environment.
4. Improves communication and budget allocation.
By using a CISO dashboard, CISOs can drill down and prioritize business areas in urgent need of security-related improvements. This helps them communicate these valuable insights to other business stakeholders. Through informed communication, CISOs can now demand higher business investment in security monitoring tools and solutions. Additionally, business stakeholders can fully understand the company’s security posture and monitor the business value of their investments.
5. Facilitates a faster response to security incidents and reduces operator workload.
With an AI-powered CISO dashboard, CISOs have real-time visibility of their company’s security posture and attack surfaces. By analyzing cybersecurity data from the dashboard, IT security teams can respond quickly to cybersecurity incidents and data breaches.
A CISO dashboard highlights the most vulnerable users in the organizations – along with the reasons that make them susceptible to threats. CISOs can also utilize dashboards for data on the most prominent types of attacks and the costs incurred from each attack.
Elevating Cybersecurity with Xoriant’s “CISO Eye” Analytics Dashboard
Xoriant’s AI-powered CISO Eye analytics dashboard is the right solution for companies to address their cybersecurity challenges. With built-in features like dynamic risk assessment and automated security alerts, the dashboard allows the CISO to view and anticipate and then respond to threats efficiently, keeping the organization steps ahead of security breaches and experiencing a real-time, comprehensive security management at your fingertips with clear actionable insights.
Additionally, this CISO Eye analytics dashboard can streamline compliance management at various levels, including:
- Line of business (LOB): Product, Service, and Business
- Location: for instance, North America, India, and Singapore
- Customer, project or a business unit
- Technology including :
- Data loss prevention (DLP)
- Email security
- Identity & Access Management
- Endpoint detection and response (EDR)
- Cloud Security
- Application security
- Information security compliance training compliance
- Vertical security – including network security, endpoint security, and application security
- Real-time tracking of security incidents
- Cybersecurity budget spending – including account-based and location-based spending
Xoriant’s CISO Eye Analytics dashboard can improve the security posture by:
- Accelerating the detection of security misconfigurations and risks.
- Reducing manual work so security teams can focus on high-value tasks.
- Providing a real-time view of the organization’s security posture and attack surfaces.
- Providing detailed insights into cybersecurity investments and existing resources.
Business Outcomes
With its visual representation and real-time insights, a CISO dashboard is an effective tool for modern-day CISOs to navigate the complexities of cyber incident security controls and their efficacy. With Xoriant’s CISO analytics dashboard implemented, an organization is able to perform compliance tracking and monitoring for:
- Over 60+ security control parameters and associated performance and risk indicators
- Over 8000+ Endpoint security
- Email Security
- Application security
- Line of business across 4 geographical locations
- Real-time open risks – top 10
- Regulatory compliance – ISO27K open NCs
At Xoriant, our cybersecurity services have enabled our customers to reduce their data breach costs by 50%. With our AI-powered dashboard, CISOs can make informed decisions by accessing real-time security data with actionable insights. Are you looking to simplify your security compliance? We can help. Contact us now.


 View Previous Article
View Previous Article




